Protect your organization’s most valuable asset: information. The ISO 27001 Extension helps you implement and maintain an Information Security Management System (ISMS) within Artintech ERP — covering risk assessment, controls, incident management, and compliance documentation.

Overview: ISO/IEC 27001:2022 is an international standard for Information Security Management Systems (ISMS). It helps organizations systematically manage information security through a risk-based approach, encompassing people, processes, and technology.
Key Specifications and Requirements:
Benefits of Implementation:
Required Checklists:
Documentation Required for Certification Audit:
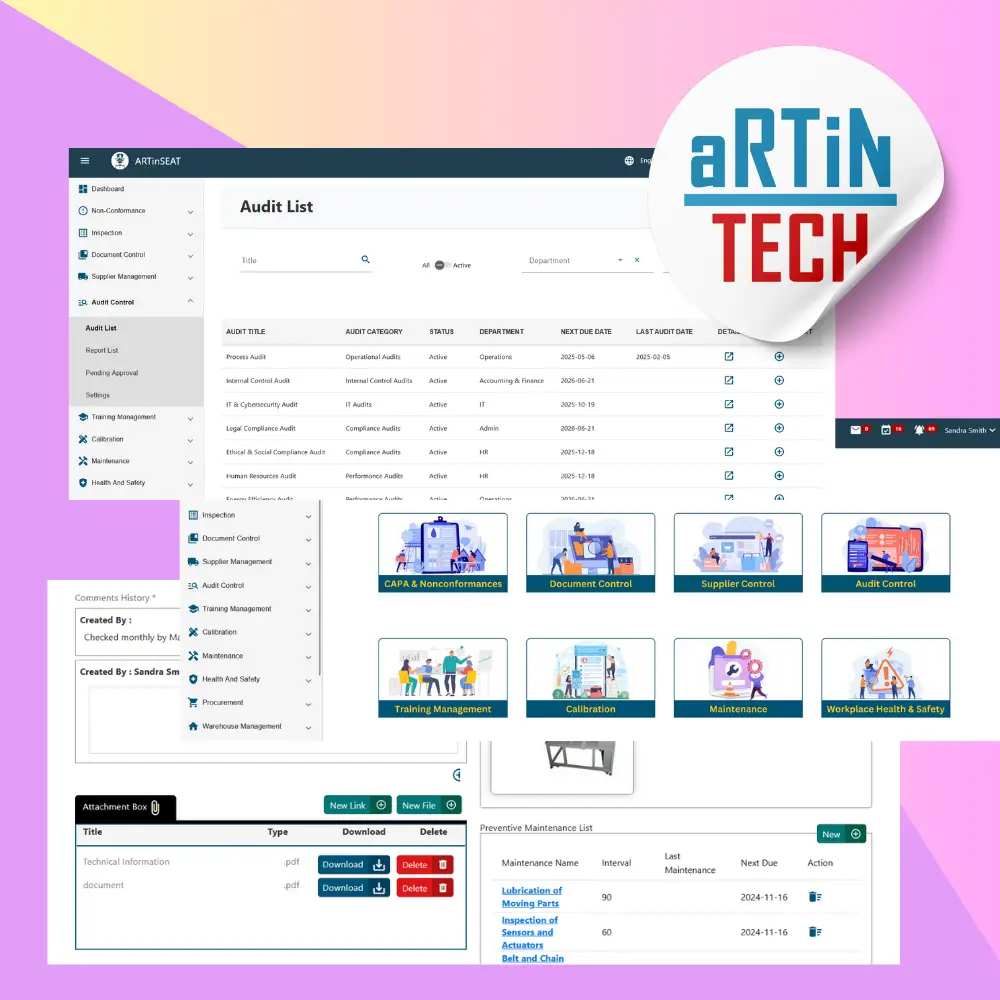
Information Asset Register
Risk Assessment & Treatment Plan
Control Implementation Tracker
Incident & Breach Logging
Policy Management System
Internal Audit & Monitoring
Data Protection: Enforce secure practices across all departments.
Audit Readiness: Maintain complete documentation trail for ISO audits.
Continuous Vigilance: Active monitoring, breach response, and user accountability.
Policy Control: Ensure every policy is reviewed, approved, and acknowledged.
Finance & Legal: Protect sensitive documents and transactions.
Healthcare: Control access to patient and health data.
Manufacturing & Engineering: Prevent IP theft and control access to systems.
SMEs: Achieve ISO 27001 compliance without the burden of siloed systems.
Acquiring this extension gives you two paths for implementation, ensuring a perfect fit for your organization’s needs and resources.
Let the experts at GQCC handle everything. This white-glove service includes full project management, data migration, user training, and hands-on support through your final certification audit.
Ideal for teams with strong internal resources. GQCC will provide expert guidance, a clear project plan, and key training sessions, empowering your team to lead the deployment.
Contact us to schedule a consultation for system setup and audit alignment.
